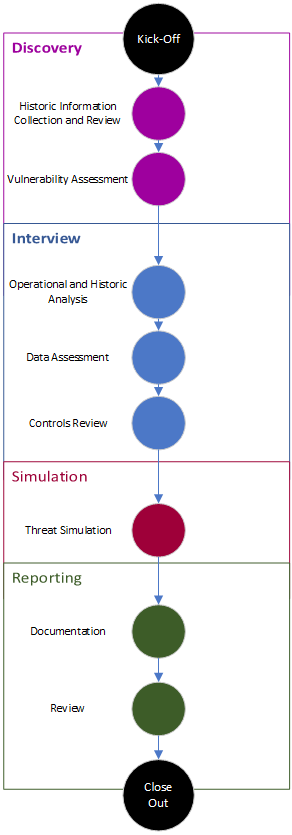
RISK ASSESSMENTS
Risk assessments serve as the very core of virtually every cybersecurity regulation, framework, and governance model. Risk assessments help companies catalog the likelihood and impact that cyber, physical, and other threats will exploit weaknesses and vulnerabilities within the environment. The end goal of a risk assessment is to provide an actionable plan for remediating weaknesses and alleviating risk in the future. This is realized by Partners in Regulatory Compliance (PIRC) hand-written, prioritized remediation statements for every area of risk discovered through the risk assessment process.
These assessments serve as a baseline from which organizations can then launch into future planning, policy work, and budgeting. Too often, organizations spend money on technical controls, then wrap policy around those controls, and finally ask a third-party to “grade the paper” via a risk assessment.
PIRC advocates for a change to this methodology. In fact, in our view, the entire order of operations should be flipped. Companies should perform risk assessments first, then use their risk baseline to inform and guide written policy, and then use that policy to direct hardware, software, and other purchasing decisions around risk mitigation controls.
PIRC follows the NIST SP800-30 Guide for Conducting Risk Assessments approach. This methodology was created in 2002 and later revised in 2012 to its current form. It was created through collaborative efforts by a joint task force (JTF). The JTF included members of the DoD, other federal agencies, and the private sector. We follow the NIST standard for risk assessments because it is the de facto standard for performing risk assessments, regardless of regulation, vertical, or location.
Also see: Cybersecurity Assessment Services