Did you know that the global, average cost for a data breach is $3.92 million? This staggering amount was reported by IBM in its 2019 Cost of a Data Breach Report. There are several actions that businesses can take to decrease their chance of a data breach, but one of the more straightforward ways to prevent unscrupulous entities from gaining access to important online accounts is to add a multi-factor authentication (MFA) mechanism.
Multi-Factor Authentication Defined
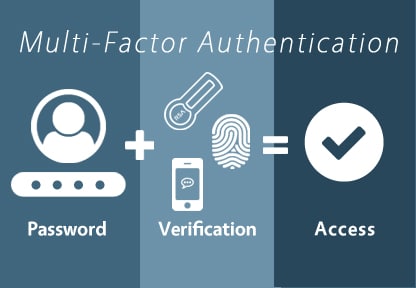
Multi-factor authentication requires users to enter more than one — typically two — pieces of information to gain access to an account. Enabling MFA whenever possible minimizes the risk that your business’ important data will be compromised. MFA adds another layer of security on top of passwords, making it harder for your accounts to be breached. The computing power available to a hacker with relative ease is staggering these days, so it is necessary now more than ever to enable MFA when possible. Moreover, adding a multi-factor authentication (MFA) mechanism to thwart unauthorized access can aid in organizational compliance with several regulations including the NY SHIELD Act, the California Consumer Protection Act (CCPA), and others. In fact, multifactor authentication for compliance reasons is one of the reasons that companies like Duo are seeing extraordinary uptake right now.
Multi-factor authentication is typically divided into three main categories. These are:
- Knowledge factors are things you know. These can be things like answers to secret questions.
- Possession factors that refer to things you own, such as security tokens or key fobs.
- Inherence factors rely on your biological characteristics. These factors typically rely on biometric data like retinal scan data and fingerprint scans.
To illustrate a simple example of how MFA works, consider logging into your banking institution’s online portal to carry out a transaction. Your company could implement a possession factor via an authentication application on a smartphone. When logging in, you would have to enter your password, as well as a one-time code generated by the authenticator app.
Multi-factor Authentication Support Technology
A list of websites that support MFA can be viewed at Two Factor Auth. This is a great resource that can help employees to decide if they should even use a service that hosts sensitive data. Here are a few ways that authentication factors are implemented:
- SMS – With this option, a code is sent via text message. This code must be entered after you enter your password.
- Authenticator apps – Authenticator apps generate codes based on a secret key. These apps display time-sensitive codes which must be entered after your password on login.
- Security Tokens – These are hardware devices that authorize access to a network service.
Wrapping Up
To wrap up, MFA is critically important for businesses. It can help to prevent potentially expensive data breaches, protecting your company’s and customers’ sensitive data in the process. In addition, it can help to ensure that your business is in compliance with various data security regulations.
If you are interested in learning more about our solutions related to multifactor authentication for compliance, contact us.